About Me
I started my career in IT security after obtaining a B.S. and M.S. in Cognitive Science from UT Dallas. I worked in a Security Operations Center (SOC) for an MSSP monitoring security appliances and performing PCI compliance reporting for about a year before returning to school at SMU Guildhall to pursue a professional certificate in game programming.
Following my graduation from Guildhall, I worked for a startup on a variety of projects, including a multiplayer augmented reality defense-shooter game, automated web application testing via UI and API, and cloud infrastructure codification and deployment of web applications. Near the end of my time at the startup I had developed an interest in broader software development beyond games and how to leverage the cloud.
I obtained my first AWS certification and then, with a background in security and software development, took a role in security engineering. Since then, I have continued to work in both Azure and AWS, supporting teams in deploying, monitoring, and maintaining secure cloud infrastructure and applications.
I am currently an individual contributor (IC) but have also held both lead and managerial roles in security engineering. I am a self-starter whose primary passion is learning, evaluating, and applying new technologies and techniques to securely meet business needs. I enjoy sharing knowledge with others via teaching, documentation, knowledge sessions, and mentorships, and I am experienced with security monitoring, testing, controls, and response, cloud technologies, automation, and writing, debugging, and deploying code.
Work Experience
defi SOLUTIONS partners with captives, banks, credit unions, and finance companies of all types and sizes to help lenders transform their operations. The company’s comprehensive suite of end-to-end originations, servicing, and analytics solutions, together with technology-enabled processing services, are flexible, configurable, and scalable to address the ever-evolving needs of lenders and borrowers.
- Security engineering strategy, leadership, and mentoring
- Security-related planning, research, and input for new technology and architecture initiatives, including weekly meetings with VPs/CIO
- Security process and control design, documentation, and knowledge transfer
- Commercial cloud security security-related incident escalations
- Escalations related to security automation, IAM, and SSO
- Technical audit escalations
- Continuing hands-on implementation and review in areas of cloud privileged IAM, application identity and credential management, and SSO (OIDC and SAML-based integrations)
defi SOLUTIONS partners with captives, banks, credit unions, and finance companies of all types and sizes to help lenders transform their operations. The company’s comprehensive suite of end-to-end originations, servicing, and analytics solutions, together with technology-enabled processing services, are flexible, configurable, and scalable to address the ever-evolving needs of lenders and borrowers.
- Technical audit participation and evidence provisioning
- Primary POC for potential security incidents
- Configuration and management of SAST and DAST application security tooling, including CI/CD integration
defi SOLUTIONS partners with captives, banks, credit unions, and finance companies of all types and sizes to help lenders transform their operations. The company’s comprehensive suite of end-to-end originations, servicing, and analytics solutions, together with technology-enabled processing services, are flexible, configurable, and scalable to address the ever-evolving needs of lenders and borrowers.
- Azure security posture analysis, monitoring, and improvement, using tools including Defender for Cloud, Azure Policy, and Sentinel
- Security task automation via PowerShell scripting and Azure Pipelines (CI/CD), including management of application identities and secrets and secure storage via Azure Key Vault
- Virtual security appliance deployment (via IaC), configuration, and operation, including log forwarders and vulnerability scanners
- IAM design, implementation, and administration using SSO, MFA, RBAC, and PIM
- Management and configuration of corporate security tooling including endpoint threat detection, DLP, CASB, and vulnerability scanning
HookBang is a Creative Technology Studio that provides full-service software design and development for brands, agencies, and technology companies with hard problems.
- Cloud infrastructure codification and deployment via AWS CloudFormation and Ansible
- Jenkins configuration maintenance
- Integration and deployment management, monitoring, and improvement
- Application development and bug fixing in Node.js and Python, including front-end and back-end components
HookBang is a Creative Technology Studio that provides full-service software design and development for brands, agencies, and technology companies with hard problems.
- Mobile AR game development with Unity
- Automated software testing via UI and API
- Serverless web app development using Python, AWS Lambda, and API Gateway
- Cloud resource load testing
NetBoundary, Inc. dba 1440 Security is a Managed Security Service Provider (MSSP) utilizing industry- leading tools to perform log management, intrusion detection and prevention, vulnerability assessment scanning, and firewall management.
- Monitoring security appliances such as IDS/IPS, Log Management, and SIEMs
- Researching and responding to security incidents
- PCI compliance reporting
Education
SMU Guildhall
Cert., Game Programming
2015 - 2017
Programming students at SMU Guildhall practice each of the many facets of gameplay programming as well as the study of game engine architectures, both in commercial engines and their own game engine, which they’ll build from the ground up.
At SMU Guildhall I focused on deepening my understanding of programming for video games. I worked on a number of individual and team-based projects, including a self-authored game engine in C++, a local multiplayer CTF shooter in Unreal, and a VR puzzle game using the HTC Vive.
UT Dallas
MS Applied Cognition and Neuroscience
2012 - 2014
The Master of Science in Applied Cognition and Neuroscience degree (ACN) provides students with advanced training that incorporates methodologies and approaches from such diverse fields as neuroscience, experimental psychology, artificial intelligence, and human-computer interactions.
Following my undergraduate degree, I continued my education at UT Dallas in a graduate program that was customizable to my interests. I took courses in psychology, game programming, and mathematical modeling of intelligent systems, and I worked in an on-campus research lab studying tinnitus.
UT Dallas
BS Cognitive Science
2008 - 2012
Cognitive science focuses on the understanding of intelligent systems, both biological and artificial. These can range from people and animals to web search engines, computers and robots.
During my undergraduate degree at UT Dallas, I took courses in mathematics, computer science, psychology, and neuroscience, all part of a multidisciplinary approach to understanding information processing in humans and machines.
Certifications & Skills
Certifications
- Certified Information Systems Security Professional (May 2022)
- Microsoft Certified: Azure Security Engineer Associate (May 2020)
- Microsoft Certified: Azure Fundamentals (Sep 2019)
- AWS Certified Solutions Architect - Associate (May 2019)
- Microsoft Technology Associate: Windows Operating System Fundamentals (Jan 2015)
- Apple Certified Associate - Mac Integration 10.9 (Nov 2014)
- Microsoft Technology Associate: Security Fundamentals (Nov 2014)
- CompTIA A+ (Aug 2009)s
Languages
PowerShell, Python, JavaScript, Bash, C#, C++, Java
Skills
Identity and Credential Management, Infrastructure Security, Security Automation, Access Controls, Posture Management
Tools
Perforce, Git, Jenkins, AWS CLI/SDK, Azure CLI, Azure DevOps, Terraform, Docker, Ansible, Unity, Unreal
Projects
Any Colony, Self-Authored C++ Game Engine
Wrote a DLL plugin containing the logic necessary for an ant colony to feed itself and fight other colonies to the death in multiple maps with distinctive characteristics and composition.

- DLL created and stored all representative information about the map and the colony itself, populating this storage as more of the map was discovered and the colony grew
- Food locations were noted and claimed by individual worker ants to avoid multiple ants trying to retrieve the same food. Food was unclaimed if a worker died while trying to retrieve it
- All ants pathed using a fast implementation of A* in which the closed list was eliminated (map cells had a boolean on themselves to indicate if they were closed) and the open list consisted of map cell indices
- Cells were assigned different G costs for different ant types to facilitate more efficient and strategic exploration
Steering Behaviors, Self-Authored C++ Game Engine
Implemented steering behaviors in personal engine including Seek/Flee, Arrive, Path Follow, Wander, and Pursue/Evade.
- Seek/Flee calculates a vector to the target and accelerates in that direction (the negative of that direction in the case of Flee).
- Arrive, which is essentially a variant of Seek, has a radius around the target within which it throttles its velocity (proportional to the distance to the target) so that it comes to a nice smooth stop instead of overshooting like Seek does
- Path Follow picks targets along a path and calculates a vector to the current target along the path and accelerates in that direction. Once the agent is within a certain radius of the target point the next point along the path is set as the current target for the behavior
- Wander has a circle centered a certain distance out along the forward vector of the agent. The agent picks a random point along the outer edge of this circle to accelerate toward to produce a meandering behavior
- Pursue/Evade is similar to Seek/Flee but instead of calculating a vector to the target to accelerate to it calculates a vector to a predicted position of the target after a certain amount of time to move toward (move away from in the case of Evade). This results in a more aggressive seeking behavior than Seek itself
2D Roguelike, Self-Authored C++ Game Engine
Creation of a 2D roguelike game with different types of procedural map generators, a field of view system for agent sight, pathfinding for agent movement, a combat system, AI behaviors from C++ classes, interactable features in the environment, and saving and loading.

- A* pathfinding was used by entities to move to random locations and to the position of the player. The algorithm could be invoked generically and supported visualization of the pathfinding process and the final path returned
- Entity behaviors were data-driven using XML so that creating a new behavior was as simple as creating the .hpp and .cpp files and referencing them in the XML
SimpleMiner, Self-Authored C++ Game Engine
SimpleMiner is a simple Minecraft clone developed by myself over 8 weeks.
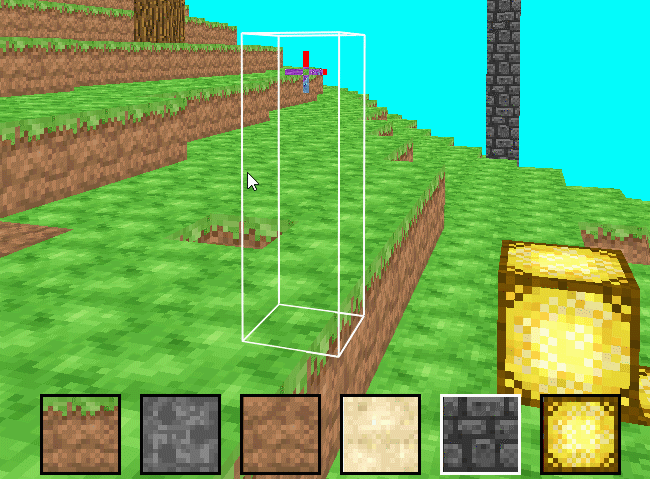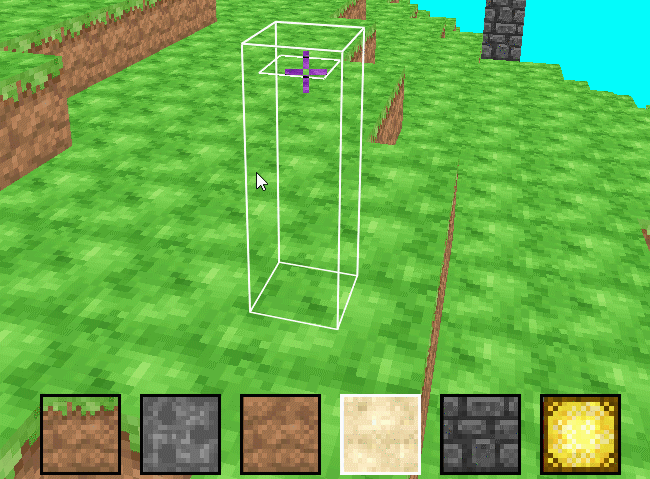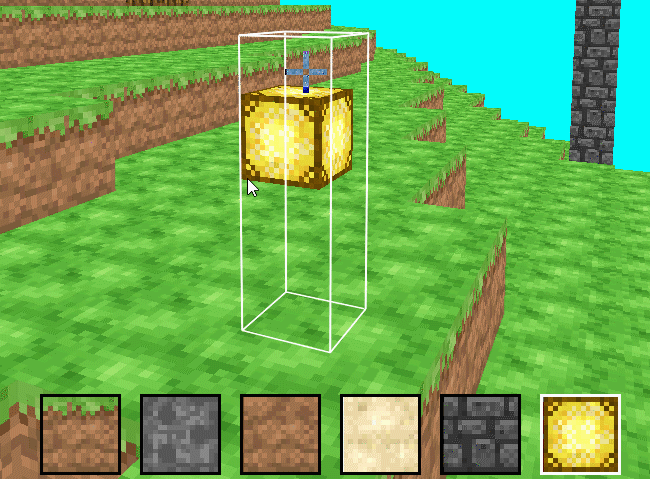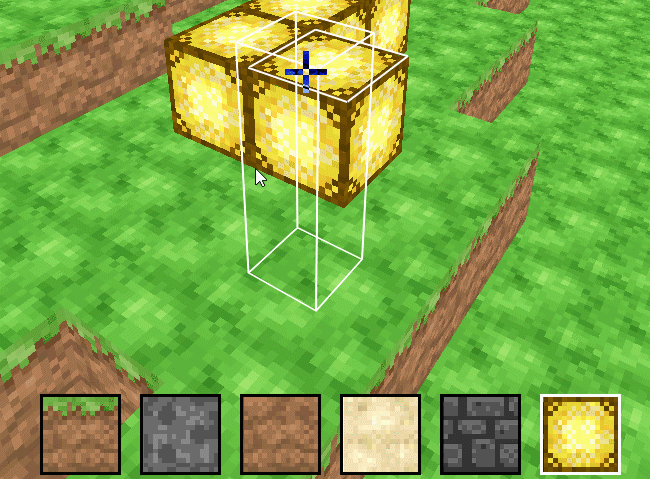
- Chunks of blocks are rendered using vertex arrays (VAs), one VA per chunk
- New chunks are generated using Perlin noise as they come within a certain view range of the player
- Old chunks are efficiently saved out to disk (RLE compression) and then deleted from memory after they go out of range
- Chunks previously saved out are reloaded (instead of regenerated) if they come back into range
- Block selection, digging, and placing are all implemented
- Basic player physics such as jumping and bounding box collision are implemented
- Trees are placed using Perlin noise during chunk generation and are consistent across chunk boundaries
- Optimized performance with bitwise operators, interior hidden surface removal, and chunk rendering frustum culling